If you have running production server you should use firewall to protect your server from any attacks outside your network. Well, today we will teach you on how to install ConfigServer Security & Firewall (CSF) and Login Failure Daemon (LFD) on Rocky Linux 8.5 (Green Obsidian). CSF is actually Stateful Packet Inspection (SPI) firewall with Login Intrusion Detection system and Security tools for Linux-based server. Where the SPI iptables firewall include comprehensive, straight-forward, easy and flexible to configure.
It’s support almost all Linux-based operating system, including RedHat Enterprise Linux 7/8 and its derivatives including CentOS 7/8, RockyLinux 8, CloudLinux 7/8, CloudLinux 7/8, AlmaLinux 8, Debian 8/9/10/11, Ubuntu 18.04 – 20.04 LTS, and Slackware 12. The CSF and LFD suite is include some features such as Straight-forward SPI iptables firewall script, Permanent and Temporary (with TTL) IP blocking, Excessive connection blocking, Suspicious process reporting, Exim SMTP AUTH, and much more.
There are several virtualizations type which support CSF and LFD like KVM, Xen, VMware, VirtualBox, Mod_security failures (v1 and v2), Password protected web pages (htpasswd), Allow Dynamic DNS IP addresses, and MS Virtual Server. While the Login Failure Daemon (LFD) run every time and periodically (every X seconds) scans the latest log file entries for login attempts against the server like Brute-force attacks. Stay calm if you have running web-based control panel since CSF and LFD suites have UI Integration to manage the Firewall rules, including cPanel-WHM, DirectAdmin, Plesk, InterWorx, Webmin, CyberPanel, VestaCP, and CentOS Web Panel (CWP).
CSF and LFD suites having advanced features and extensive knowledge of Linux-based server based on their experience on cloud server environment, server security, cPanel-WHM, Exim and MailScanner. For cPanel server service you will get secure tools to securing your server from any attack, perform server tunning to solve load issues, and check for exploits issues inside the system.
Well, today we will guide you on how to install ConfigServer Security & Firewall (CSF) and Login Failure Daemon (LFD) on Rocky Linux 8.5 (Green Obsidian). Make sure to meet the following requirenments before installing CSF and LFD suites.
PRE-REQUISITES:
* VPS, Cloud, or Bare-Metal Server * Running on Rocky Linux OS 8.5 (Green Obsidian) * Server IPv4 Address * Superuser Privileges (Sudo Access) * Gnome Terminal for Linux Desktop * PuTTy SSH Client for Windows or Mac * Powershell for Windows 10/11
1.) Install CSF & LFD Suites
Move to the temporary directory
$ cd /tmp
Download the CSF and LFD Suites file using the following command
$ wget https://download.configserver.com/csf.tgz
Extract the archieve file
$ tar -xzf csf.tgz
Move to the CSF Firewall directory
$ cd csf
Run the CSF installer
$ sh install.sh
2.) Check Iptables Mode
After CSF and LFD suites installed on your node, you can run the following command to check the iptables mode (if required).
On newly deployed Rocky Linux 8.5 machine, you can use yum or dnf commands on dnf-enabled system.
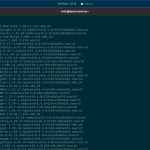
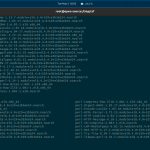
$ yum install iptables DigitalOcean Agent 108 kB/s | 3.3 kB 00:00 DigitalOcean Droplet Agent 79 kB/s | 3.3 kB 00:00 Dependencies resolved. ===================================================================================================================================================== Package Architecture Version Repository Size ===================================================================================================================================================== Installing: iptables x86_64 1.8.4-20.el8 baseos 584 k Installing dependencies: iptables-libs x86_64 1.8.4-20.el8 baseos 106 k libibverbs x86_64 35.0-1.el8 baseos 334 k libnetfilter_conntrack x86_64 1.0.6-5.el8 baseos 63 k libnfnetlink x86_64 1.0.1-13.el8 baseos 32 k libnftnl x86_64 1.1.5-4.el8 baseos 82 k libpcap x86_64 14:1.9.1-5.el8 baseos 168 k pciutils x86_64 3.7.0-1.el8 baseos 104 k rdma-core x86_64 35.0-1.el8 baseos 58 k Transaction Summary ===================================================================================================================================================== Install 9 Packages Total download size: 1.5 M Installed size: 4.0 M Is this ok [y/N]: y
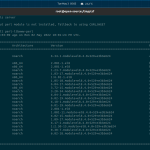
$ perl /usr/local/csf/bin/csftest.pl Testing ip_tables/iptable_filter...OK Testing ipt_LOG...OK Testing ipt_multiport/xt_multiport...OK Testing ipt_REJECT...OK Testing ipt_state/xt_state...OK Testing ipt_limit/xt_limit...OK Testing ipt_recent...OK Testing xt_connlimit...OK Testing ipt_owner/xt_owner...OK Testing iptable_nat/ipt_REDIRECT...OK Testing iptable_nat/ipt_DNAT...OK RESULT: csf should function on this server
3.) Configure CSF Rule
Then you can configure the CSF rule like adding a new SSH port number, change RESTRICT_SYSLOG, and much more. Simply edit csf.conf file.
$ nano /etc/csf/csf.conf
4.) Enable or disable CSF and LFD Suites
Don’t forget to enable CSF and LFD Suites by editing the csf.conf file.
To disable CSF and LFD Suites
# Disable >> TESTING = "1"
To enable CSF and LFD Suites
# Enable >> TESTING = "0"
Don’t forget to set RESTRICT_SYSLOG to 3. Then save the file using CTRL + O + ENTER and exit using CTRL + X.
# RESTRICT_SYSLOG = "3"
Or you can use the following command to enable or disable CSF and LFD Suites.
To enable CSF LFD via command
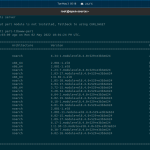
$ csf -e *WARNING* URLGET set to use LWP but perl module is not installed, fallback to using CURL/WGET csf and lfd are not disabled!
Let’s install perl module to solve the issues.
$ yum install perl-libwww-perl Last metadata expiration check: 0:03:09 ago on Mon 02 May 2022 10:01:24 PM UTC. Dependencies resolved. ===================================================================================================================================================== Package Architecture Version Repository Size ===================================================================================================================================================== Installing: perl-libwww-perl noarch 6.34-1.module+el8.4.0+529+e3b3e624 appstream 212 k Installing dependencies: perl-Compress-Raw-Bzip2 x86_64 2.081-1.el8 baseos 39 k perl-Compress-Raw-Zlib x86_64 2.081-1.el8 baseos 67 k perl-Data-Dump noarch 1.23-7.module+el8.4.0+529+e3b3e624 appstream 36 k perl-Digest-HMAC noarch 1.03-17.module+el8.4.0+529+e3b3e624 appstream 19 k perl-Digest-SHA x86_64 1:6.02-1.el8 appstream 65 k perl-Encode-Locale noarch 1.05-10.module+el8.4.0+529+e3b3e624 appstream 20 k perl-File-Listing noarch 6.04-17.module+el8.4.0+529+e3b3e624 appstream 17 k perl-HTML-Parser x86_64 3.72-15.module+el8.4.0+529+e3b3e624 appstream 118 k perl-HTML-Tagset noarch 3.20-34.module+el8.4.0+529+e3b3e624 appstream 23 k perl-HTTP-Cookies noarch 6.04-2.module+el8.4.0+529+e3b3e624 appstream 38 k perl-HTTP-Date noarch 6.02-19.module+el8.4.0+529+e3b3e624 appstream 18 k perl-HTTP-Message noarch 6.18-1.module+el8.4.0+529+e3b3e624 appstream 99 k perl-HTTP-Negotiate noarch 6.01-19.module+el8.4.0+529+e3b3e624 appstream 21 k perl-IO-Compress noarch 2.081-1.el8 baseos 257 k perl-IO-HTML noarch 1.001-11.module+el8.4.0+529+e3b3e624 appstream 27 k perl-LWP-MediaTypes noarch 6.02-15.module+el8.4.0+529+e3b3e624 appstream 28 k perl-NTLM noarch 1.09-17.module+el8.4.0+529+e3b3e624 appstream 23 k perl-Net-HTTP noarch 6.17-2.module+el8.4.0+529+e3b3e624 appstream 42 k perl-TimeDate noarch 1:2.30-15.module+el8.4.0+529+e3b3e624 appstream 52 k perl-Try-Tiny noarch 0.30-7.module+el8.4.0+529+e3b3e624 appstream 44 k perl-WWW-RobotRules noarch 6.02-18.module+el8.4.0+529+e3b3e624 appstream 22 k Transaction Summary ===================================================================================================================================================== Install 22 Packages Total download size: 1.3 M Installed size: 2.6 M Is this ok [y/N]: y
To disable CSF LFD via command
$ csf -x
5.) Custom Rule on CSF and LFD Suites
You can also create custom rules or editing into the CSF firewall. Simply edit the csf.pignore file, then add your custom rules to the bottom line of this file. For example as follow.
$ nano /etc/csf/csf.pignore # Custom Rules exe:/usr/sbin/varnishd exe:/usr/sbin/nginx exe:/usr/sbin/httpd
6.) Restart CSF and LFD Suites
Don’t forget to restart CSF and LFD Suites using the following command.
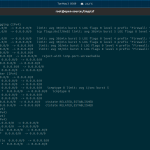
$ csf -r Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `POSTROUTING' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `POSTROUTING' csf: FASTSTART loading DROP no logging (IPv4) LOG tcp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *TCP_IN Blocked* " LOG tcp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 tcp flags:0x17/0x02 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *TCP_OUT Blocked* " LOG udp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *UDP_IN Blocked* " LOG udp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *UDP_OUT Blocked* " LOG icmp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *ICMP_IN Blocked* " LOG icmp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *ICMP_OUT Blocked* " DROP all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 REJECT all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 reject-with icmp-port-unreachable DENYOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 DENYIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ALLOWOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ALLOWIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 csf: FASTSTART loading Packet Filter (IPv4) DROP all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 INVALID tcp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 INVALID tcp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 8 limit: avg 1/sec burst 5 LOGDROPIN icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 8 ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT icmp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ctstate RELATED,ESTABLISHED ACCEPT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ctstate RELATED,ESTABLISHED csf: FASTSTART loading TCP_IN (IPv4) csf: FASTSTART loading TCP_OUT (IPv4) csf: FASTSTART loading UDP_IN (IPv4) csf: FASTSTART loading UDP_OUT (IPv4) ACCEPT all opt -- in lo out * 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT all opt -- in * out lo 0.0.0.0/0 -> 0.0.0.0/0 LOGDROPOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 LOGDROPIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 csf: FASTSTART loading DNS (IPv4) LOCALOUTPUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 LOCALINPUT all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 *WARNING* Binary location for [SENDMAIL] [/usr/sbin/sendmail] in /etc/csf/csf.conf is either incorrect, is not installed or is not executable *WARNING* Binary location for [HOST] [/usr/bin/host] in /etc/csf/csf.conf is either incorrect, is not installed or is not executable *WARNING* Missing or incorrect binary locations will break csf and lfd functionality
Let’s solve these HOST and SENDMAIL issue with the following commands.
Install BIND Utility
$ yum install bind-utils DigitalOcean Agent 87 kB/s | 3.3 kB 00:00 DigitalOcean Droplet Agent 72 kB/s | 3.3 kB 00:00 Dependencies resolved. ===================================================================================================================================================== Package Architecture Version Repository Size ===================================================================================================================================================== Installing: bind-utils x86_64 32:9.11.26-6.el8 appstream 450 k Installing dependencies: bind-libs x86_64 32:9.11.26-6.el8 appstream 173 k bind-libs-lite x86_64 32:9.11.26-6.el8 appstream 1.2 M bind-license noarch 32:9.11.26-6.el8 appstream 101 k fstrm x86_64 0.6.1-2.el8 appstream 28 k protobuf-c x86_64 1.3.0-6.el8 appstream 36 k python3-bind noarch 32:9.11.26-6.el8 appstream 149 k Transaction Summary ===================================================================================================================================================== Install 7 Packages Total download size: 2.1 M Installed size: 4.9 M Is this ok [y/N]: y
Configure SENDMAIL
$ echo '#!/bin/sh' > /usr/sbin/sendmail $ chmod +x /usr/sbin/sendmail
Restart again the CSF Service
$ csf -r Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `LOGDROPIN' Flushing chain `LOGDROPOUT' Flushing chain `DENYIN' Flushing chain `DENYOUT' Flushing chain `ALLOWIN' Flushing chain `ALLOWOUT' Flushing chain `LOCALINPUT' Flushing chain `LOCALOUTPUT' Flushing chain `INVDROP' Flushing chain `INVALID' Deleting chain `LOGDROPIN' Deleting chain `LOGDROPOUT' Deleting chain `DENYIN' Deleting chain `DENYOUT' Deleting chain `ALLOWIN' Deleting chain `ALLOWOUT' Deleting chain `LOCALINPUT' Deleting chain `LOCALOUTPUT' Deleting chain `INVDROP' Deleting chain `INVALID' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `POSTROUTING' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `OUTPUT' Flushing chain `PREROUTING' Flushing chain `INPUT' Flushing chain `FORWARD' Flushing chain `OUTPUT' Flushing chain `POSTROUTING' csf: FASTSTART loading DROP no logging (IPv4) LOG tcp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *TCP_IN Blocked* " LOG tcp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 tcp flags:0x17/0x02 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *TCP_OUT Blocked* " LOG udp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *UDP_IN Blocked* " LOG udp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *UDP_OUT Blocked* " LOG icmp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 0 level 4 prefix "Firewall: *ICMP_IN Blocked* " LOG icmp opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 limit: avg 30/min burst 5 LOG flags 8 level 4 prefix "Firewall: *ICMP_OUT Blocked* " DROP all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 REJECT all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 reject-with icmp-port-unreachable DENYOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 DENYIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ALLOWOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ALLOWIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 csf: FASTSTART loading Packet Filter (IPv4) DROP all opt -- in * out * 0.0.0.0/0 -> 0.0.0.0/0 INVALID tcp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 INVALID tcp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 8 limit: avg 1/sec burst 5 LOGDROPIN icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 icmptype 8 ACCEPT icmp opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT icmp opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 ctstate RELATED,ESTABLISHED ACCEPT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 ctstate RELATED,ESTABLISHED csf: FASTSTART loading TCP_IN (IPv4) csf: FASTSTART loading TCP_OUT (IPv4) csf: FASTSTART loading UDP_IN (IPv4) csf: FASTSTART loading UDP_OUT (IPv4) ACCEPT all opt -- in lo out * 0.0.0.0/0 -> 0.0.0.0/0 ACCEPT all opt -- in * out lo 0.0.0.0/0 -> 0.0.0.0/0 LOGDROPOUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 LOGDROPIN all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0 csf: FASTSTART loading DNS (IPv4) LOCALOUTPUT all opt -- in * out !lo 0.0.0.0/0 -> 0.0.0.0/0 LOCALINPUT all opt -- in !lo out * 0.0.0.0/0 -> 0.0.0.0/0
$ lfd -r
7.) Verify Installed CSF Version
You can also verify which CSF version installed on your Rocky machine.
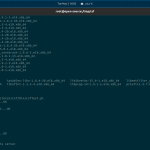
$ csf -v csf: v14.16 (generic)
CONCLUSION:
We have successfully install and configure CSF and LFD Suites in order to deploy more secure environment to hosted all of your website or your client website, either it running under cPanel/WHM, Plesk, DirectAdmin or other web-based control panel.