OpenSSH is a major connectivity tools for remote login under SSH protocol that mostly used on Linux-based server. If you have currently running Linux-based server, either it VPS, Cloud or Bare-Metal, you should familiar with this remote login tools. OpenSSH offers many benefits to encrypts all traffic over remote connections, including eliminating eavesdropping, hijacking connection and other attacks during remote connections into the target server is occurs.
There are large suite of secure tunneling capabilities you can found on OpenSSH, including advanced configuration options, and several authentication methods. Here are the important tools bundled on OpenSSH Suite.
1.) Remote operations or connection are done using SSH, SCP, and sFTP. 2.) Key Management with SSH-Add, SSH-Keysign, SSH-Keyscan, and SSH-Keygen. 3.) Service side include SSHD, sFTP-Server, and SSH-Agent.
Currently OpenSSH is developed and maintenanced directly by several developers under OpenBSD Project. It’s owned by OpenBSD Foundation, a Canadian-based federal non-profit organization founded by the OpenBSD Project as a “single point of contact for persons and organizations requiring a legal entity to deal with when they wish to support OpenBSD.” OpenSSH was first released under a BSD-license in July 1996 (25 years ago). Altough OpenSSH is incorporated to many commercial products, but very few companies make financial contributions to OpenBSD. So, you can send your contributions to support OpenSSH via OpenBSD Foundation.
Well, today we will guide you on how to change SSH/SSHD Port Number on Rocky Linux 8.5 (Green Obsidian). It should be done in your end to create more secure environment rather than using default SSH Port Number. Before moving into the next step, make sure to meet the following requirenments.
PRE-REQUISITES:
* VPS, Cloud, or Bare-Metal Server * Running on Rocky Linux OS 8.5 (Green Obsidian) * Server IPv4 Address * Superuser Privileges (Sudo Access) * Gnome Terminal for Linux Desktop * PuTTy SSH Client for Windows or Mac * Powershell for Windows 10/11
1.) Login to Your Machine via SSH Terminal
On this guide we will use Windows 10 machine to create remote connections into our Linux-based server which is hosted on Digital Ocean or commonly known as droplets. And of course, we can utilize Windows PowerShell to connect or login into the remote server.
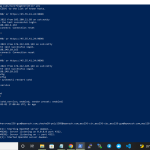
PS C:\Users\fcgid> ssh [email protected] -p22 The authenticity of host '45.55.41.24 (45.55.41.24)' can't be established. ECDSA key fingerprint is SHA256:6C0gRTo0YQcklE/nuj+6hgO2fDCQUAd4e3r8BJo03/M. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '45.55.41.24' (ECDSA) to the list of known hosts. [email protected]'s password: Web console: https://open-source.project:9090/ or https://45.55.41.24:9090/ Last failed login: Mon May 2 16:37:39 UTC 2022 from 103.200.21.89 on ssh:notty There were 2996 failed login attempts since the last successful login. Last login: Sun May 1 19:51:13 2022 from 180.248.4.163
2.) Adding Port Number on Firewall Rules
Next, if you have active Firewall running on your machine, eg ConfigServer Security & Firewall (CSF) and Login Failure Daemon (LFD), so you must adding your new SSH Port Number into Firewall Rules. Simply open the csf.conf file with the following commands and then add your new SSH port number into TCP_IN and TCP_OUT sections. You can using your prefered Linux editor like nano or vim.
For example, your new SSH Port number is 4322, so simply add this port number into TCP_IN/OUT sections like the following examples.
--------------------------------------------------------------- # Allow incoming TCP ports TCP_IN = "25,53,80,110,143,443,465,587,993,995,4322" # Allow outgoing TCP ports TCP_OUT = "25,53,80,110,113,443,587,993,995,4322" # Allow incoming UDP ports UDP_IN = "53,80,443" # Allow outgoing UDP ports # To allow outgoing traceroute add 33434:33523 to this list UDP_OUT = "53,113,123" ---------------------------------------------------------------
Then restart your CSF and LFD using below command.
$ csf -r $ lfd -r
3.) Change SSH Port Number on sshf_config File
After that simply edit the ssdh_config file to change the default SSH Port number (port 22) to the new SSH port number which is more secure, eg port 4322. Then change the default port 22 into port 4322, and don’t forget to uncomment that line. As you can see on the following code.
$ nano /etc/ssh/sshd_config --------------------------------------------------------------- # If you want to change the port on a SELinux system, you have to tell # SELinux about this change. # semanage port -a -t ssh_port_t -p tcp #PORTNUMBER # Port 4322 #AddressFamily any #ListenAddress 0.0.0.0 #ListenAddress :: ---------------------------------------------------------------
4.) Restart SSH/SSHD Service
On the last step simply restart the SSH/SSHD service using the following simple command.
$ systemctl restart sshd
Or
$ service sshd restart Redirecting to /bin/systemctl restart sshd.service
5.) Re-Login to the Remote Server
Don’t forget to try re-login into your remote server using a new port number 4322, it’s only to verify that your SSH configurations is correctly. So, you won’t be accidentally blocked into your own server.
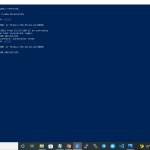
Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. Try the new cross-platform PowerShell https://aka.ms/pscore6 PS C:\Windows\system32> ssh [email protected] -p4322 [email protected]'s password: Web console: https://open-source.project:9090/ or https://45.55.41.24:9090/ Last failed login: Mon May 2 16:57:23 UTC 2022 from 51.15.190.11 on ssh:notty There were 6 failed login attempts since the last successful login. Last login: Mon May 2 16:54:18 2022 from 180.248.10.163 [root@open-source ~]#
5.) Manage OpenSSH Services
On Linux-based server you can use the following command to managed OpenSSH service.
To Start OpenSSH Services $ systemctl start sshd
To Stop OpenSSH Services $ systemctl stop sshd
To Restart OpenSSH Services $ systemctl restart sshd
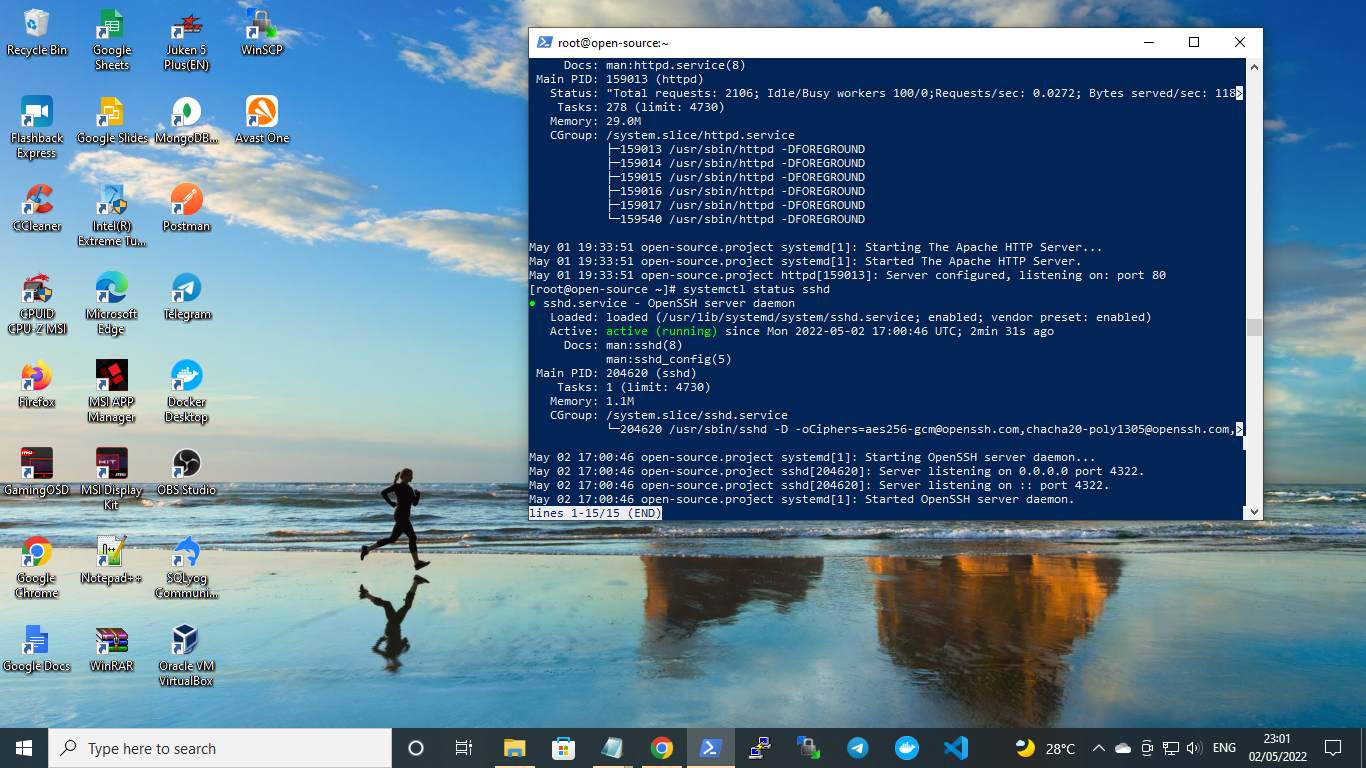
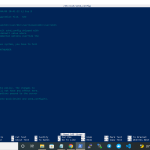
To Check Status of OpenSSH Services $ systemctl status sshd ● sshd.service - OpenSSH server daemon Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled; vendor preset: enabled) Active: active (running) since Mon 2022-05-02 17:00:46 UTC; 31min ago Docs: man:sshd(8) man:sshd_config(5) Main PID: 204620 (sshd) Tasks: 1 (limit: 4730) Memory: 2.8M CGroup: /system.slice/sshd.service └─204620 /usr/sbin/sshd -D [email protected],[email protected],aes256-ctr,aes256-> May 02 17:00:46 open-source.project sshd[204620]: Server listening on :: port 4322. May 02 17:00:46 open-source.project systemd[1]: Started OpenSSH server daemon. May 02 17:07:53 open-source.project sshd[204857]: Accepted password for root from 180.248.10.163 port 51330 ssh2 May 02 17:07:53 open-source.project sshd[204857]: pam_unix(sshd:session): session opened for user root by (uid=0) May 02 17:20:46 open-source.project sshd[205250]: Accepted password for root from 180.248.10.163 port 62770 ssh2 May 02 17:20:46 open-source.project sshd[205250]: pam_unix(sshd:session): session opened for user root by (uid=0) May 02 17:27:22 open-source.project sshd[205506]: Accepted password for root from 180.248.10.163 port 62870 ssh2 May 02 17:27:22 open-source.project sshd[205506]: pam_unix(sshd:session): session opened for user root by (uid=0) May 02 17:32:15 open-source.project sshd[205702]: Accepted password for root from 180.248.10.163 port 59646 ssh2 May 02 17:32:15 open-source.project sshd[205702]: pam_unix(sshd:session): session opened for user root by (uid=0) lines 1-21/21 (END)
CONCLUSION:
You have successfully change the SSH Port number from the default port 22 into secure port number, 4322. You can apply this guide to all of your Linux-based server, either it VPS, Cloud or Bare-Metal server which running under Rocky Linux 8.5 (Green Obsidian) or other Linux distros.